Overview
Making connections to a Cassandra cluster that uses SSL can be a little tricker than usual, however properly securing your client connections with SSL is important, especially if you are connecting to your cluster via the Internet or an untrusted network.
Pre-requisites
Before we get started you’ll first need to install the Java Cryptography Extensions. You can download the version corresponding to your installed Java version (use $> java -version to find this out) from Oracle:
Once downloaded, extract the contents of the archive to the lib/security subdirectory of your JRE’s installation directory:
- Mac: /Library/Java/JavaVirtualMachines/jdk1.8.0_72.jdk/Contents/Home/jre/lib/security/13
- Linux: /usr/lib/jvm/java-8-oracle/jre/lib/security/14
- Windows: C:\Program Files\Java\jdk1.8.0_72\jre\lib\security\
Note that Windows versions of DataStax DevCenter may bundle it’s own version of Java. In this case you’ll need to install the JCE extensions to the bundled JRE’s security directory. To check this open “About DevCenter”, then “Installation Details”, then switch to the “Configuration” tab and find “java.home=…”.
CQLSH
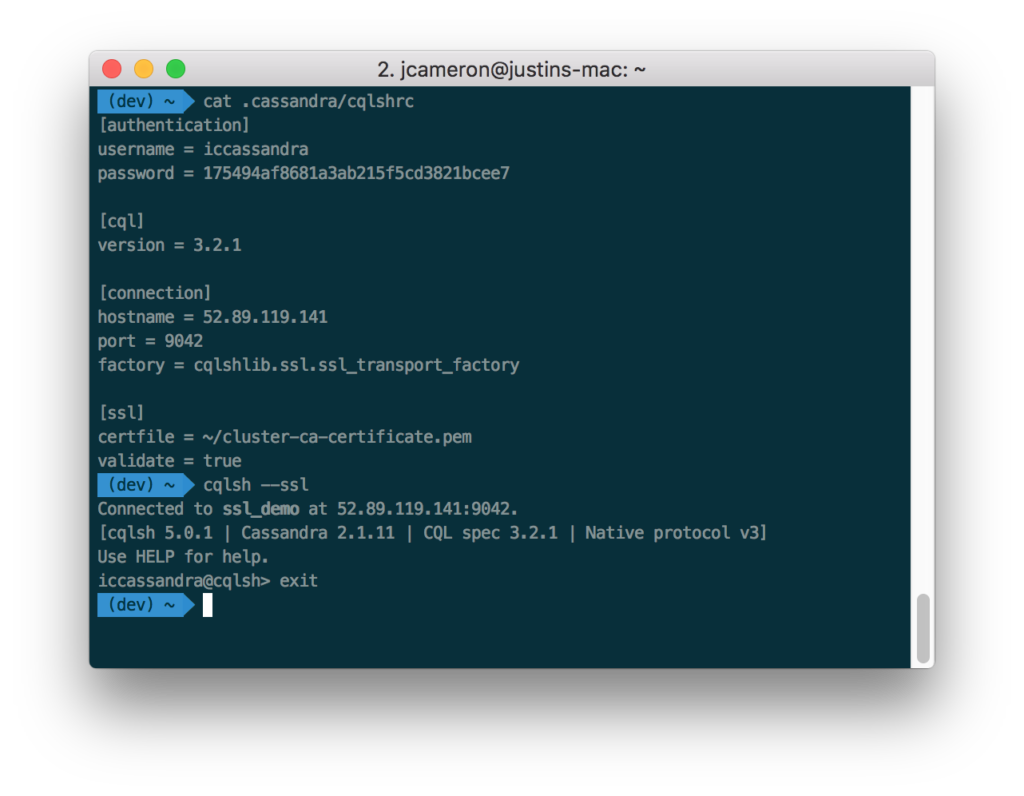
First, create a new cqlsh configuration file at ~/.cassandra/cqlshrc, using the template below.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
[authentication] username = myusername password = mypassword [cql] ; Substitute for the version of Cassandra you are connecting to. version = 3.1.7 [connection] hostname = 127.0.0.1 port = 9042 factory = cqlshlib.ssl.ssl_transport_factory [ssl] certfile = /path/to/cluster-ca-certificate.pem ; Note: If validate = true then the certificate name must match the machine's hostname validate = true ; If using client authentication (require_client_auth = true in cassandra.yaml) you'll also need to point to your uesrkey and usercert. ; SSL client authentication is only supported via cqlsh on C* 2.1 and greater. ; This is disabled by default on all Instaclustr-managed clusters. ; userkey = /path/to/userkey.pem ; usercert = /path/to/usercert.pem |
You’ll need to fill in the Cassandra username and password, the CQL version corresponding to the cluster you’re connecting to, the hostname, and a path to the SSL certitficate. If you are using Instaclustr, you can find this information in the Connection Info screen in the Instaclustr management console.
If you aren’t sure what version of CQL your cluster is running, you can check the following ways:
- by querying Cassandra:
SELECT cql_version FROM system.local; - by using nodetool:
$> nodetool version - or you can just try to connect with cqlsh. If you provide the wrong cql version in your cqlshrc configuration file, Cassandra will return an error displaying the correct version.
Now you will be able to connect using $> cqlsh --ssl
If you want to connect to a different node, you can override the hostname field in the cqlshrc file by supplying an IP address, like so: $> cqlsh --ssl 127.0.0.1
Cassandra-stress
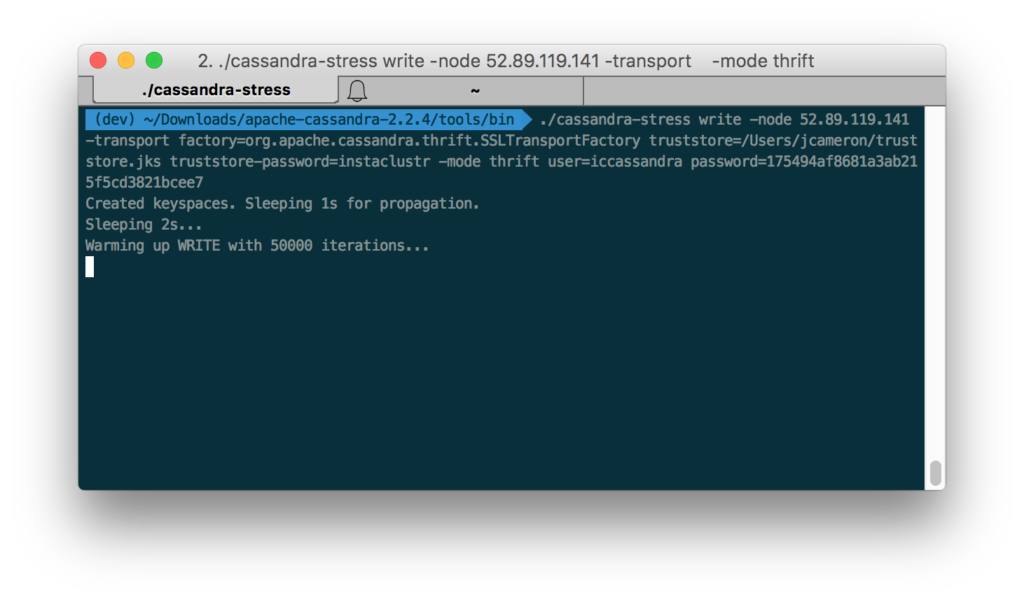
To connect to an SSL cluster using cassandra-stress, you’ll need to provide the following arguments:
$> cassandra-stress write -node 127.0.0.1 -transport truststore=/path/to/cluster/truststore.jks truststore-password=mytruststorepassword -mode native cql3 user=myuser password=mypassword
The truststore file is the Java keystore containing the cluster’s SSL certificates.
Datastax Devcenter
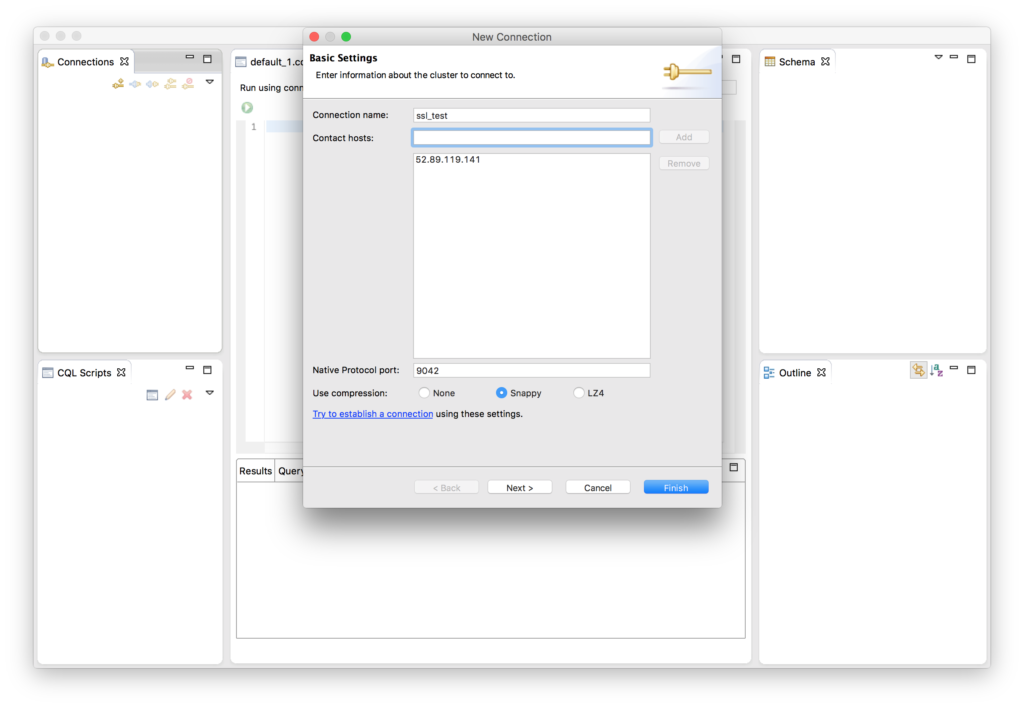
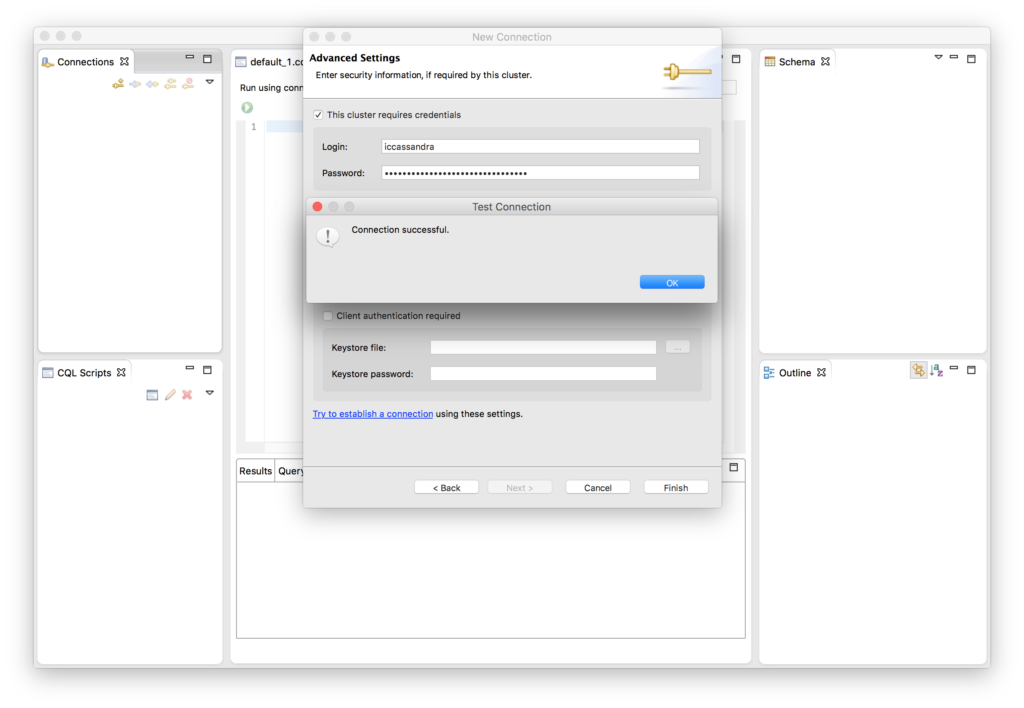
To connect to an SSL cluster using Devcenter, navigate to the File menu and choose New -> Connection. In the New Connection form, fill out the Connection Name and add one or more node IP addresses or hostnames.
Click Next.
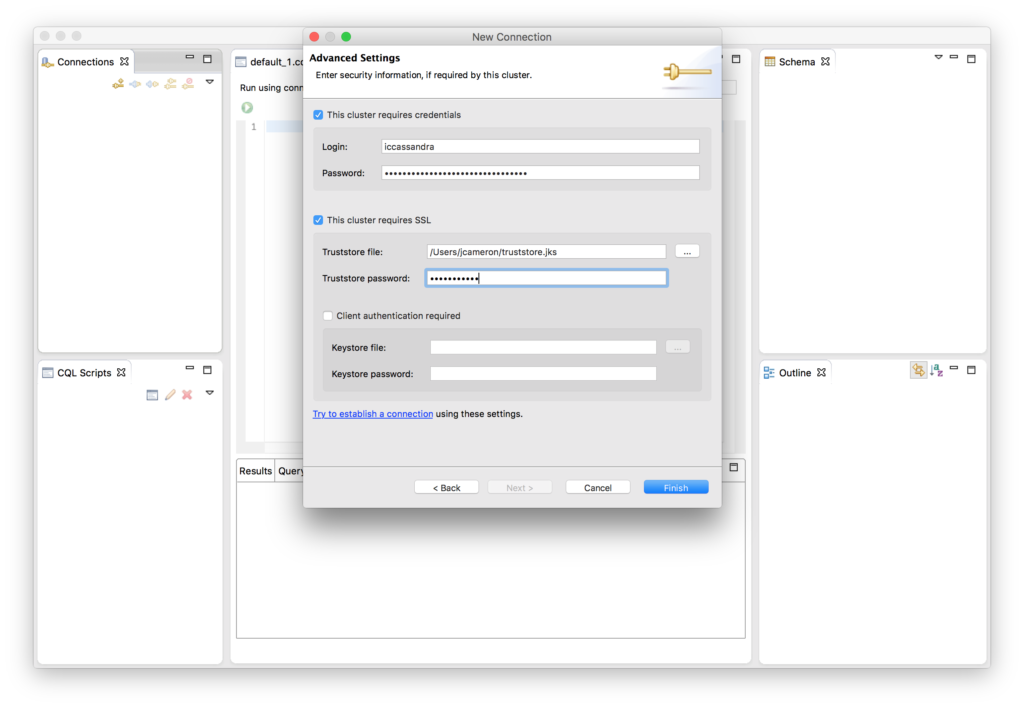
Check This cluster requires credentials and enter your Cassandra username and password if your cluster has user authentication enabled. Also check This cluster requires SSL and use the … to navigate to the Cluster’s truststore file. The truststore file is the Java keystore containing the cluster’s SSL certificates. Enter the truststore’s password.
If you have SSL client authentication enabled for your cluster (require_client_auth = True in cassandra.yaml), you must also check Client authentication required and supply a Java keystore containing your client’s SSL certificate. SSL client authentication is disabled by default for all Instaclustr-managed clusters.
Click Finish.
Devcenter will then attempt to connect to the cluster to verify the connection.